Keeping Open RAN software secure means containerizing functions, securing each container, and securing the entire software design.
Open radio access networks (Open RAN) offer a flexible and modular architecture from the radio to the network core. Open RAN brings greater flexibility in building networks through off the shelf (COTS) hardware, as opposed to using proprietary equipment. Many people, however, overlook the key benefit that comes with standardized interfaces and virtualized infrastructure: improved security.
Central to the Open RAN effort is the O-RAN Alliance, a group of leading vendors and network operators who standardize an Open RAN-based architecture for the gNodeB (gNB).
Leveraging 3GPP security in O-RAN
3GPP, defines protocols for mobile networks, specifies the gNB split into two logical functions called centralized unit (CU) and distributed unit (DU). The two entities shown in Figure 1 connect through F1-C and F1-U interfaces, as defined in 3GPP TS 38.473. [1]
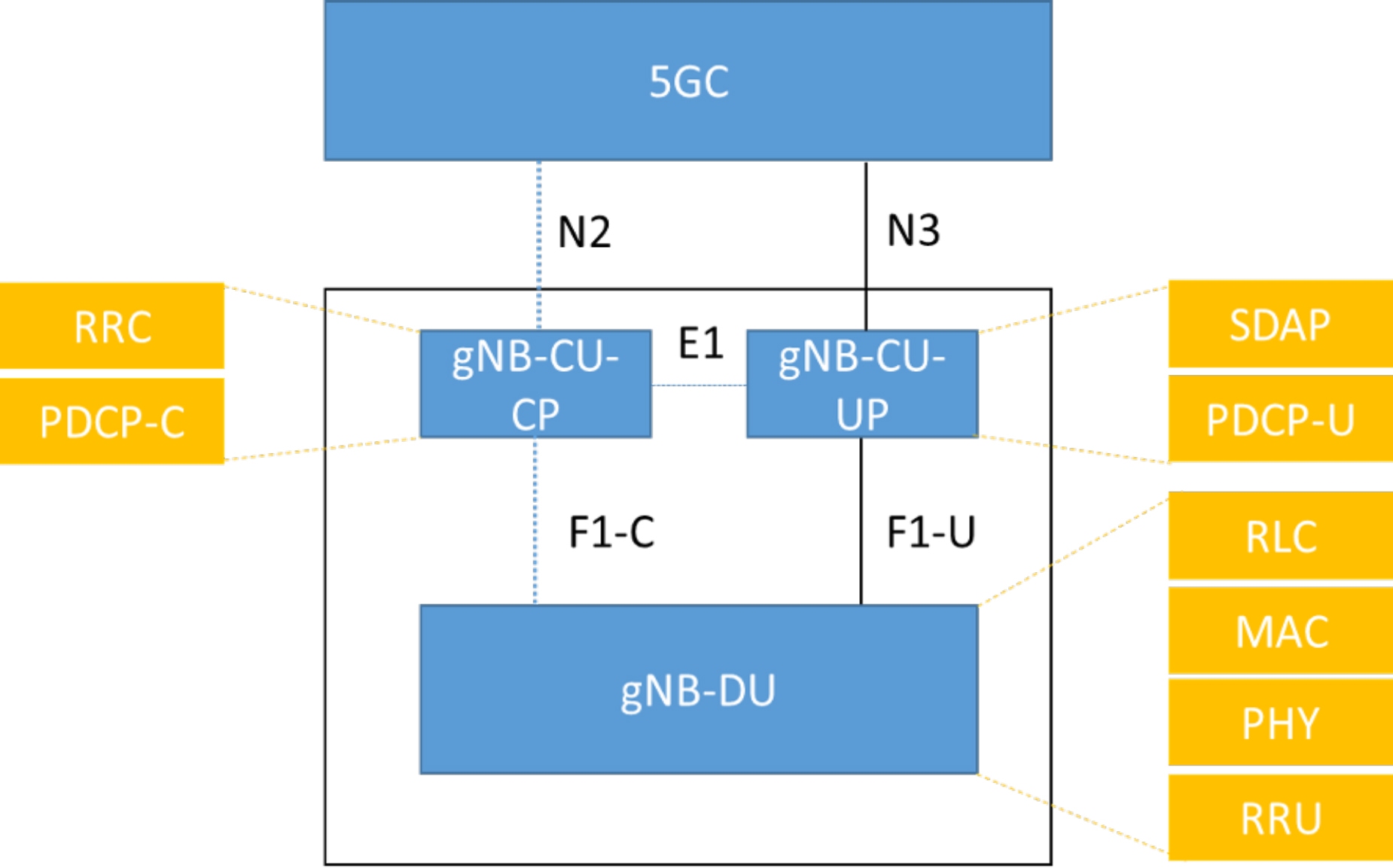
Figure 1. The gNB Logical Architecture defined by 3GPP splits functions into a centralized unit and a distribution unit.
O-RAN builds on 3GPP’s 5G new radio (NR) architecture by introducing additional interfaces, functional splits and disaggregation, shown in Figure 2.
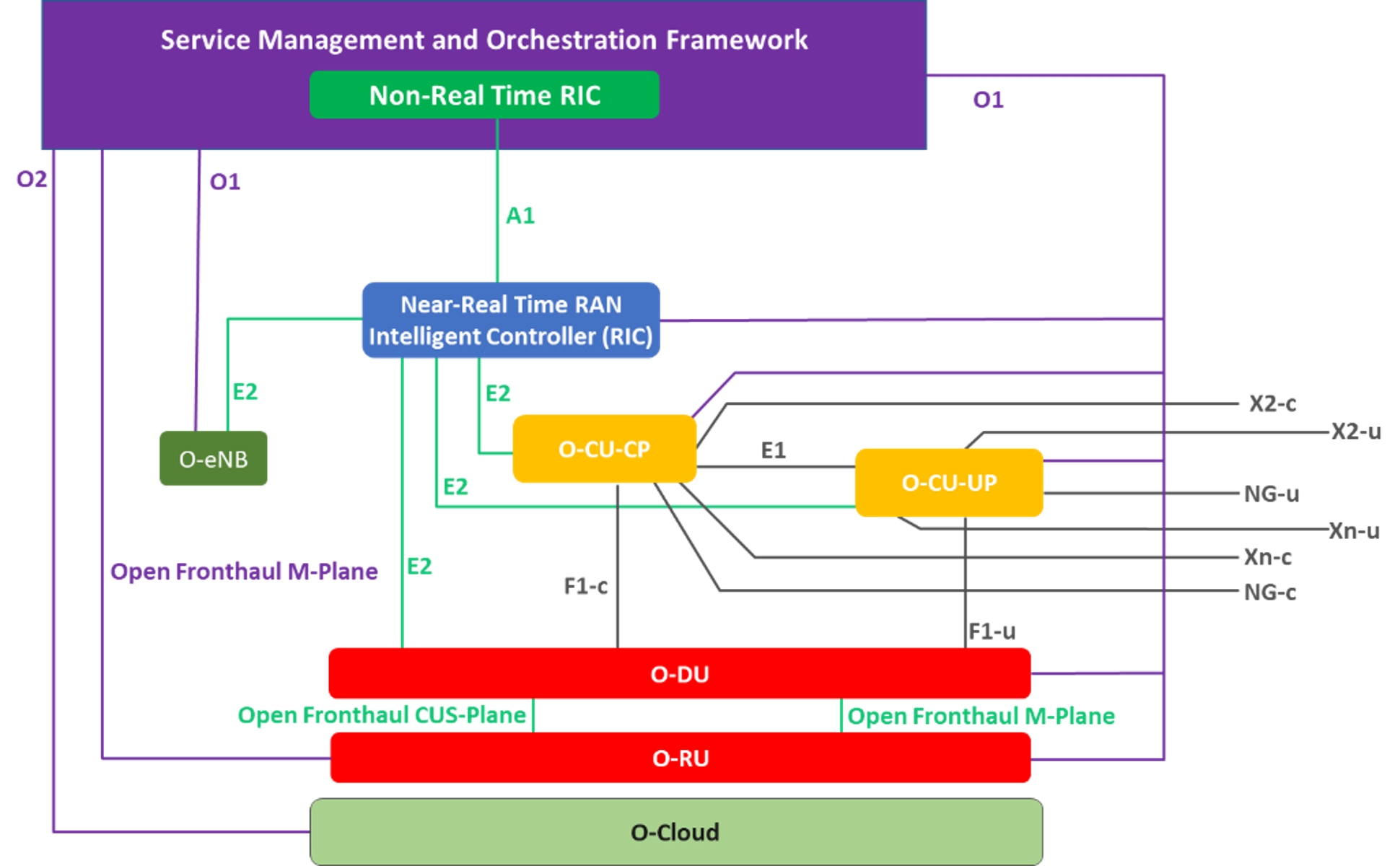
Figure 2. The O-RAN gNB logical architecture adds functional splits not present in a proprietary RAN.
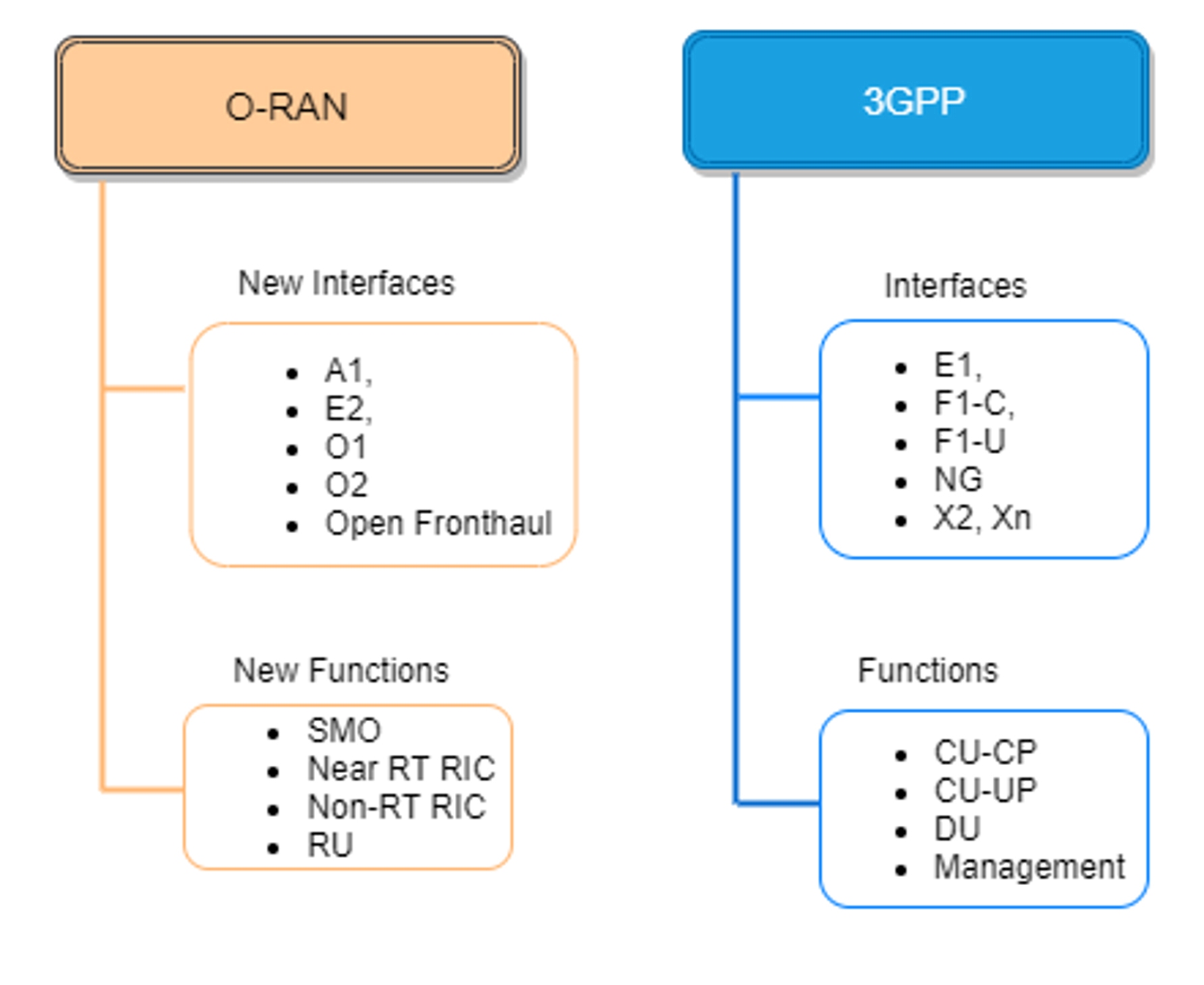
The O-RAN Alliance adds new interfaces and functions beyond 3GPP’s 5G RAN architecture. Figure 3 compares O-RAN and 3GPP standards.
Because the O-RAN Alliance builds on 3GPP’s 5G NR architecture, O-RAN benefits from 3GPP’s advanced security features introduced for 5G [2] including:
- Enhanced user identity privacy, i.e., subscription concealed identifier (SUCI).
- Full protection of control plane (CP) / user plane (UP) traffic between the user equipment (UE) and gNB (encryption and integrity protection) over the air interface.
- Full protection of gNB interfaces including the E1 interface between CU-CP and CU-UP and the F1 interface between CU and DU, as shown in Figure 2.
O-RAN security based on zero-trust architecture
Rooted in the principle of “never trust, always verify,” the zero-trust architecture (ZTA) protects modern digital environments by leveraging network segmentation, preventing lateral movement, providing layer 7 threat prevention, and simplifying granular user-access control.
O-RAN security’s ZTA is built on the following tenets:
- Secure communication between network functions
- Establishing trust based on authentication and authorization between communicating entities
- Secure platform for hosting containerized network functions
- Secure platform for O-RU
Secure communication between network functions
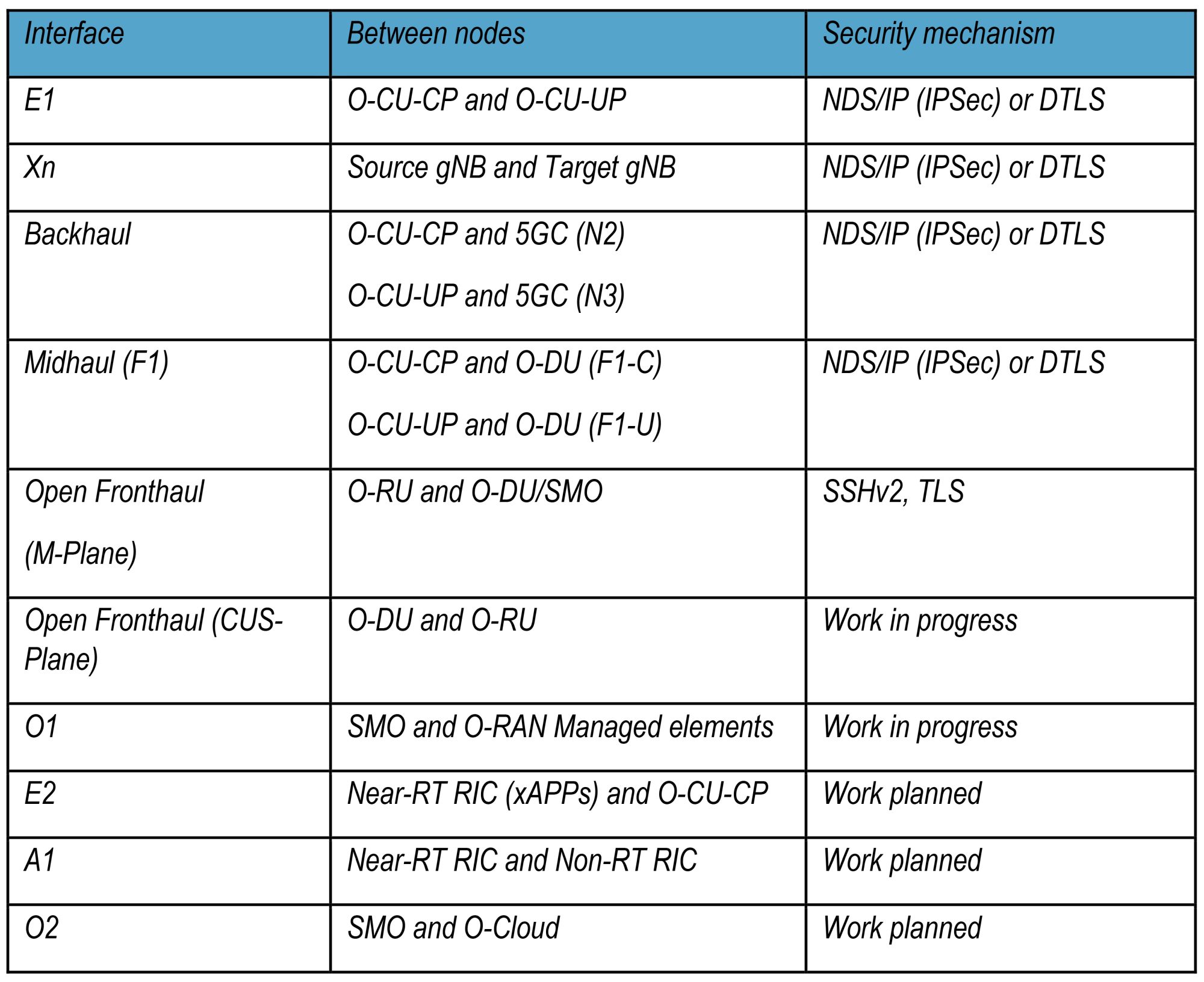
O-RAN includes “secure” interfaces between all its components. Communications exchanged on these interfaces are cryptographically protected for encryption, integrity protection and replay protection.
Table 1 summarizes the protection mechanism used for each interface in O-RAN. Italics depict interfaces specified and protected by 3GPP.
Establishing trust based on authentication and authorization
Mutual authentication is used for authenticating two entities with each other and setting up a secure encrypted connection between them. Mutual authentication prevents introduction of rogue network functions (NFs) in the network. Operator-defined X.509 certificates provide mutual authentication while establishing secure connections using IPsec and TLS protocols.
All network elements in an Open RAN — radio unit (O-RU, distribution units (O-DU) and centralized unit (O-CU) — support X.509 certificate-based authentication and related features such as auto-enrollment and auto-re-enrollment with an operator Certificate Authority (CA) server using a protocol such enrollment over secure transport (EST) or 3GPP-specified Certificate Management Protocol, CMPv2.
Secure Platform for hosting containerized Network Functions
The O-RAN architecture uses a cloud-native platform to host O-CU-CP, O-CU-UP, O-DU, Near-RT RAN intelligent controller (RIC) and non-RT RIC network functions. Figure 4 shows a typical cloud native platform with three distinct layers:
- Container-based application software
- Cloud native software stack comprising an immutable OS, Kubernetes, and Container runtime
- Cloud native hardware infrastructure
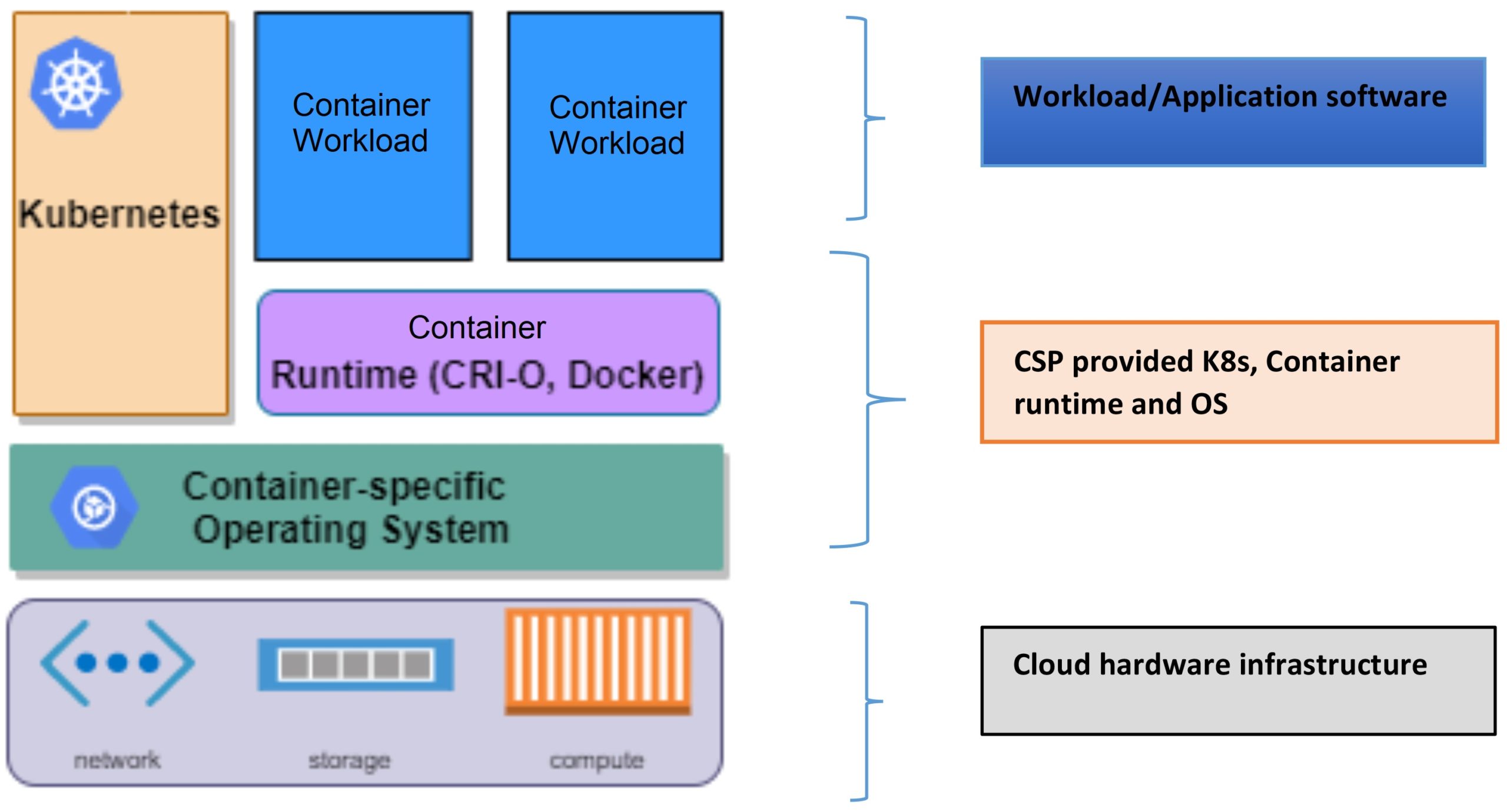
Figure 4. A cloud-native software platform consists of an immutable OS, Kubernetes, and a container runtime application.
Container security based on industry-best cloud native security principles
A workload is an application or a service deployed on the cloud. Containers offer a packaging infrastructure in which applications and dependent libraries are abstracted from the environment in which they run.
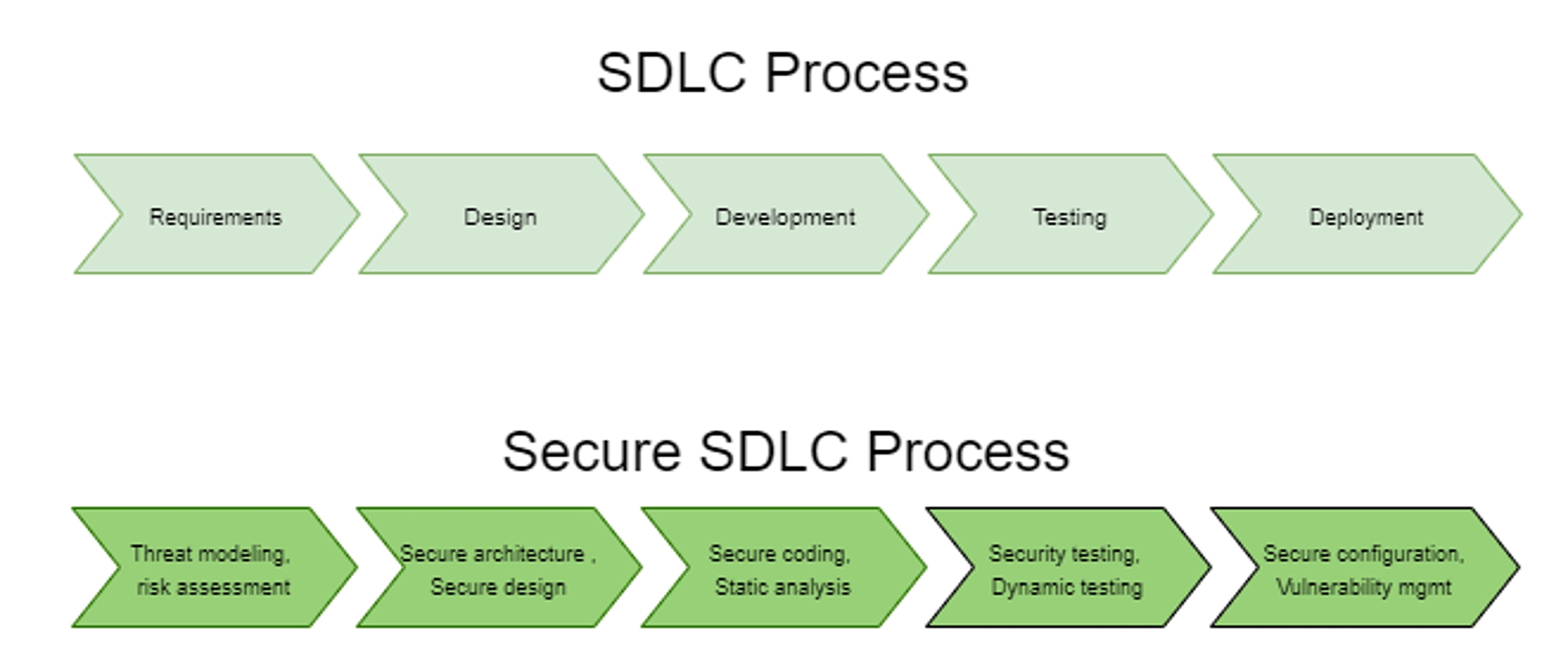
Secure-by-design enables software products to be defined from the foundation. They get their security through secure software development life cycle (S-SDLC) principles. S-SDLC integrates security testing and other security-related activities into development process. Figure 5 shows how a standard SDLC process is augmented with security practices at every stage of software development.
Using a secure SDLC process for the workloads deployed in an O-RAN network ensures early flaw detection. All stakeholders need to be aware of security considerations throughout design, development, testing, and deployment of containers. An overall reduction of intrinsic business risks for the organization also helps to create secure software.
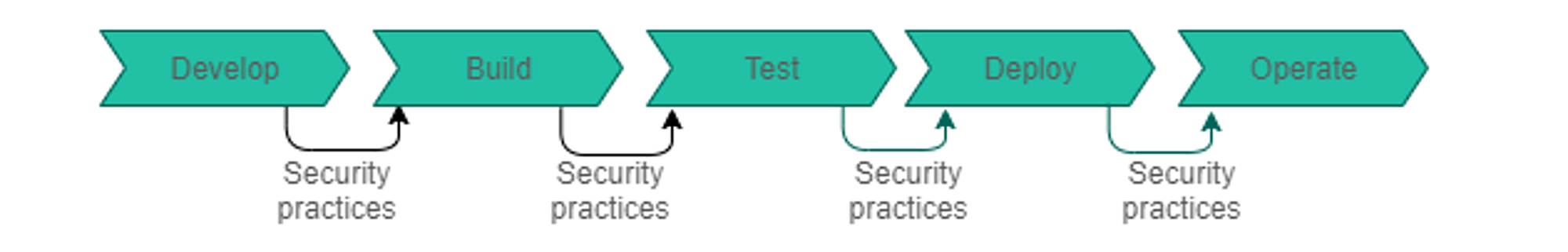
Another critical advancement in cloud-native security is the adoption of DevSecOps methodology during software development. The philosophy behind DevSecOps is to begin security testing early in the SDLC, commonly referred to as shift-left testing.
In Figure 6, DevSecOps integrates security controls into the DevOps workflow by introducing secure coding analysis using static application security testing (SAST) and automated unit, functional and integration testing.
Adoption of cloud-native architecture in Open RAN lets telecom networks take advantage of advancements in security automation and the trend in cloud computing towards “shift left.” The workloads that run in the O-RAN are validated securely (during build/deployment phase) and risk-based timely actions are taken when vulnerabilities are found before they are deployed in operator network.
In addition, use of specialized tools such as software component analysis (SCA) and container image scanning software in developing Open RAN software allows for deployment of an advanced vulnerability management process that includes automatic tracking, analysis of an application’s open source components, identification of component vulnerabilities, and tool-based vulnerability remediation. These tools are integrated into the CI/CD pipeline and provide continuous assessment of the container image.
Security aspects of a cloud native software infrastructure
A cloud native software infrastructure includes:
- Container-specific lightweight operating system,
- Container runtime that executes containers and manages container images on a node, and
- Container orchestration software such as Kubernetes for automating computer application deployment, scaling, and management that automates the deployment, management, scaling and networking of containers.
- Container orchestration software such as Kubernetes for automating computer application deployment, scaling, and management that automates the deployment, management, scaling and networking of containers. [5]
The cloud native software infrastructure relies, in line with the NIST SP 800-190 recommendations [3], on a host OS built and configured for the sole purpose of running containerized applications instead of general-purpose applications reducing the OS attack surface. In addition, the container-specific OS follows the immutability infrastructure paradigm by preventing any additional individual software package installation protecting against viruses and malware; the entire OS being managed as a single entity. The OS implements strong isolation and mandatory access control (MAC) mechanisms such as SELinux to limit what a container can do and thus protecting the OS from the containers and the containers from each other.
The cloud native software infrastructure includes a lightweight Kubernetes-specific Open Container Initiative (OCI)-compliant container runtime versioned with Kubernetes such as CRI-O to reduce the risk of vulnerabilities.
Kubernetes provides several built-in security capabilities. These capabilities secure the container environment including network security policies to control traffic between pods and clusters, capability and resource isolation, namespaces to isolate sensitive workloads, and create security boundaries, role-based access control, logging and auditing.
A cloud native O-RAN can leverage native security controls in container runtime and container orchestration platforms such as Kubernetes, to provide defense-in-depth security for the containerized workload that they host.
All virtualized platforms in an O-RAN are hardened as per 3GPP’s security assurance specifications [4] and other well-known industry benchmarks such as those from Center for Internet Security (CIS) [6]. This ensures that security controls are implemented at every layer of the platform thus reducing the platform’s attack surface.
The cloud industry has used cloud security posture management (CSPM) security tools to continuously monitor cloud environments for detection of cloud misconfiguration vulnerabilities that can lead to compliance violations and data breaches. With the adoption of a cloud native architecture in Open RAN deployments, an operator now has the means to deploy advanced CSPM tools to guard against natural “drift” of on network configuration and to reduce the potential for attacks.
Security considerations with a cloud-native hardware infrastructure
Open RAN enables decoupling of hardware and software, allowing for a platform to be built from different vendors. Zero-trust cannot be achieved without the full participation of all the elements that make up the hardware platform.
The hardware is built with a tamper resistant “hardware root of trust” device that provides a secure environment for storing cryptographic keys and for attestation of certificates and all the software running on that hardware. The device will expose a simple user interface for the application to use when it needs to use the device for storing keys, retrieving certificates, etc.
Software signing is enforced at all software layers including the firmware, cloud native software stack, and container workloads at time of deployment, as well as authenticated version upgrades to make it more difficult to introduce malicious software into operator-controlled elements.
Secure boot requires that every boot up is starting from a piece of software that cannot be updated in the field. This piece of software is referred to as core root of trust for measurement (CRTM). Thereafter, during the boot process, every software program in the platform will be integrity verified before its execution by the software at the lower layer. This establishes an end-to-end software chain of trust.
In the O-RAN deployment, it is recommended to use secure boot based on hardware root of trust and software signing to establish an end-to-end chain of trust.
Secure platform for O-RU
Security precautions on the O-RU can be divided into three aspects.
- Supply chain security
- Physical security
- Network security
Supply chain security ensures that throughout the supply chain process of manufacturing, from O-RU to its final installation site and commissioning, a controlled secure chain of custody process is followed. This ensures that the O-RU is properly tracked and tagged.
Physical security ensures that the physical O-RU is sealed with non-tamper screws that cannot be easily broken or opened and in the event of tampering or forced opening, all O-RU functionality will be disabled so that the O-RU becomes inoperable. This is in addition to all the physical and logical ports being secured and isolated, so that they cannot be used as a vulnerability entrance into the extended RAN network.
From a network security point of view, O-RU ensures that all authentication and communication security protocols are followed. Hardening features, such as disabling unnecessary software components and interfaces when not in use, running software at the correct privilege-level, scrambling/encryption of data in storage, and secure boot and hardware-based security module, are part of the comprehensive security processes on the O-RU to ward off as well as prevent unauthorized access to the O-RU.
Conclusion
The O-RAN Alliance’s architecture for RAN is built on the secure foundation of zero trust where network elements mutually authenticate with each other for them to communicate. All communication between them is transported over a secure interface per industry best practices specified by the O-RAN Alliance’s security specifications. By utilizing cloud-native architectures that have been used for years by internet service providers, data center operators and cloud service providers, O-RAN architectures have built-in data security functionality that has been hardened and improved by years of experience. These security features are transparent to mobile operators so that they know the full impact of the security features they have deployed, as well as full visibility and control over the cloud environment and network in general. O-RAN leverages several security industry best practices used in the cloud-native software development. Use of automated tools for detection, remediation of vulnerabilities in open-source software and detection, and management of secure posture provides an operator with quick detection and resolution of any security anomalies in the network.
References
- 3GPP TS 38.473: NG-RAN; F1 Application Protocol (F1AP) https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3260
- 3GPP TS 33.501: Security architecture and procedures for 5G system (Release 16). https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3169
- NIST Special Publication 800-190: Application Container Security Guide. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-190.pdf
- 3GPP TS 33.511: Security Assurance Specification (SCAS) for the next generation. Node B (gNodeB) network product class. https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3444
- Security in Open RAN White Paper https://www.altiostar.com/wp-content/uploads/2021/02/Open-RAN-Security-White-Paper-January-2021.pdf
- CIS benchmarks: https://www.cisecurity.org/cis-benchmarks/
 Nagendra Bykampadi is the Director for Product Management and Standards (Security) at Altiostar. He is also active in O-RAN Alliance and is currently the Co-Chair for the O-RAN Alliance Security Focus Group. He has over 24 years of experience in the wireless industry. In his role as the product manager for Altiostar’s product security portfolio, he is responsible for defining and managing Altiostar’s security roadmap. He is actively engaged with operators on all matters related to Open RAN security. He has also been involved in 3GPP SA3 security standardization since 2014.
Nagendra Bykampadi is the Director for Product Management and Standards (Security) at Altiostar. He is also active in O-RAN Alliance and is currently the Co-Chair for the O-RAN Alliance Security Focus Group. He has over 24 years of experience in the wireless industry. In his role as the product manager for Altiostar’s product security portfolio, he is responsible for defining and managing Altiostar’s security roadmap. He is actively engaged with operators on all matters related to Open RAN security. He has also been involved in 3GPP SA3 security standardization since 2014.





Tell Us What You Think!