Security in handoffs from cellular base stations to Wi-Fi needs help. Make your voice heard.
5G is rolling out across the world such as speed, reliability, and network efficiency. 5G is unlocking or improving use cases such as IoT communications at the edge, high quality video, lower latency to support industry controls and automation, highly-accurate location tracking, and more.
5G’s mmWave signals don’t penetrate buildings, bringing more opportunity for handover to Wi-Fi networks, commonly referred to as “Hotspot 2.0” or Passpoint by the Wi-Fi Alliance. Most consumers that use cellular don’t realize this is happening, but already Cisco reports 59% of 4G traffic will be offloaded to Wi-Fi access points (APs) by 2022. This mutually beneficial relationship between Wi-Fi and cellular lets both technologies play to their strengths. For example, no one is going to pitch designing Wi-Fi to cover a highway with cars moving 70+ MPH. Dense indoor environments are a better fit for lower cost Wi-Fi deployments.
Mobile carriers utilize Wi-Fi networks to extend network capacity to their subscribers and the transition from cellular to Wi-Fi on mobile devices is mostly transparent to the user. Unlike Wi-Fi hotspots that prompt with captive portals, users simply walk into a hotel, shopping center, airport, even their homes, and their mobile devices automatically switch from cellular to Wi-Fi. Cellular engineers working in this space need to know a few key things about the Wi-Fi networks to which their mobile subscribers’ devices are often handed off.
First, Wi-Fi as an attack surface has been neglected. Wi-Fi went mainstream in 1999, but as Figure 1 shows, there are still six Wi-Fi threat categories that operate at layer two of the OSI model. Hackers equipped with simple YouTube videos and online tools can easily exploit these threats on many Wi-Fi networks. The typical result of a Wi-Fi attack is for a third party to eavesdrop on the communication, silently intercepting usernames, passwords, credit card numbers, social profile information other valuable information.
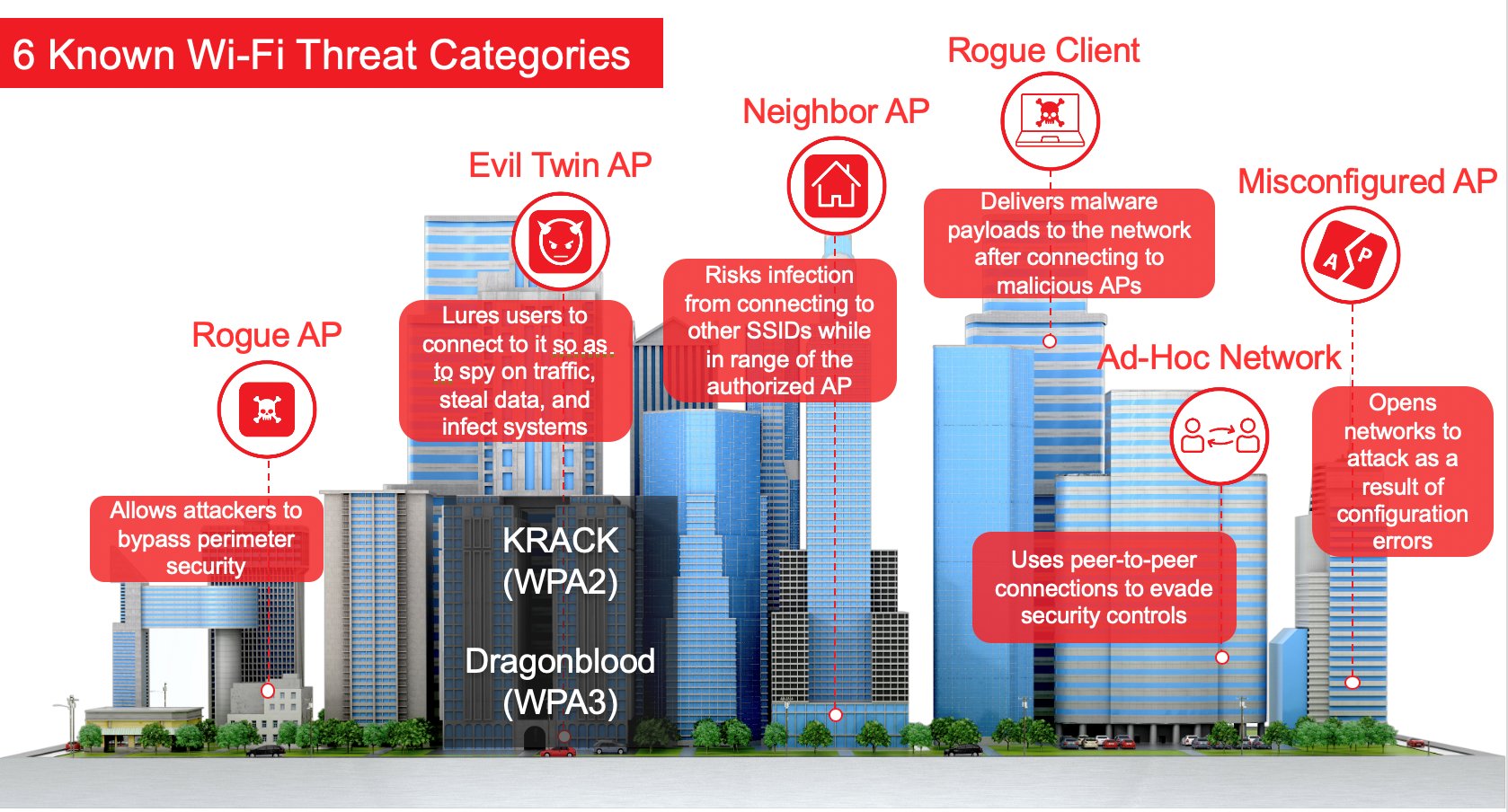
Figure 1. Hackers have six entry points with this to attack Wi-Fi networks. Image: TrustedWirelessEnvironment.com
Second, this handoff uses the enterprise option for the two main Wi-Fi authentication standards: WPA2 and WPA3. Although this is the most secure form of authentication for Wi-Fi, security researchers have already exposed vulnerabilities in one of the encryption options for enterprise authentication, MS-CHAPV2, and future research may lead to new vulnerabilities. For example, the Passpoint Deployment Guidelines (Rev 1.3) provide Table 11 (Figure 2), which describes the various credential types that may be used to authenticate a mobile device to a Wi-Fi Passpoint network. The engineers designing the system ultimately determine what credential type to use and most would not use the MS-CHAPV2 authentication method.
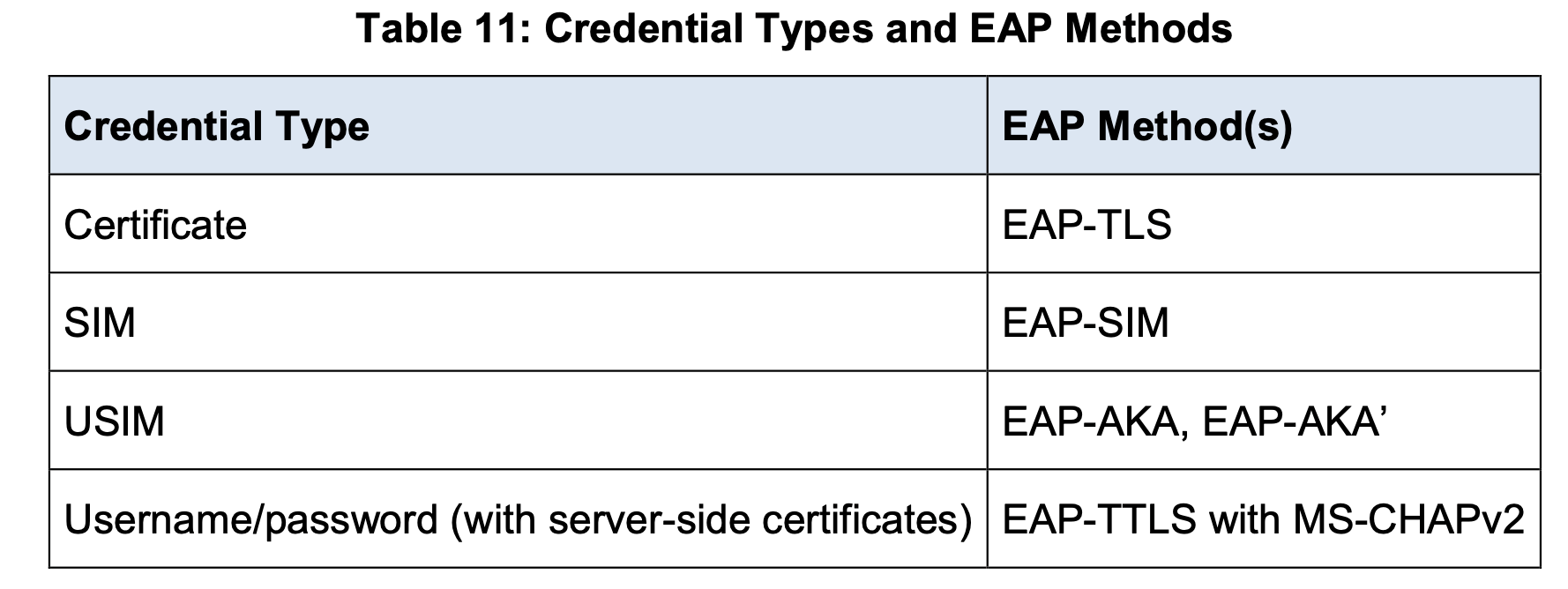
Figure 2. Table 11 from Passpoint Deployment Guidelines specifies methods and credentials for Extensible Authentication Protocol (EAP). Source: Passpoint Deployment Guidelines
For individuals concerned about possible cellular to Wi-Fi handover security vulnerabilities, a virtual private network (VPN) service can be easily utilized to encrypt communication, keeping it private from attackers who could be eavesdropping. Businesses that currently have, or are looking to deploy Wi-Fi access points (APs) with Hotspot 2.0 (Passpoint) enabled should make sure the APs they are using have been independently tested and confirmed capable of automatically detecting and preventing the six known Wi-Fi threat categories. With this Wi-Fi security in place, the business and the cellular users in that area will be safe from possible future cellular to Wi-Fi handover vulnerabilities.
Engineers working in this space also do have an opportunity to create proprietary security protection for the cellular to Wi-Fi handover attack surface. This could become a point of differentiation for various mobile carrier networks.
A more global approach to securing the cellular to Wi-Fi handover attack surface involves the power that engineers can use to help advocate for new security standards within the industry. Engineers can show their support for such an idea by signing the Trusted Wireless Environment petition here, to support an initiative aimed at building more visibility and awareness about this security issue among various standards organizations. By consciously making cellular to Wi-Fi handover security a focus among engineering teams, conferences, social networking technical groups, the wireless world can become safer for everyone.
 Ryan Orsi is Director of Product Management at WatchGuard Technologies, where he leads the company’s Secure Wi-Fi solutions portfolio. He has experience bringing disruptive wireless products to the WLAN, IoT, medical and consumer wearable markets. As a VP of Business Development in the RF industry, he led sales and business development teams worldwide to success indirect and channel environments. He holds MBA and Electrical Engineering degrees and is a named inventor on 19 patents and applications.
Ryan Orsi is Director of Product Management at WatchGuard Technologies, where he leads the company’s Secure Wi-Fi solutions portfolio. He has experience bringing disruptive wireless products to the WLAN, IoT, medical and consumer wearable markets. As a VP of Business Development in the RF industry, he led sales and business development teams worldwide to success indirect and channel environments. He holds MBA and Electrical Engineering degrees and is a named inventor on 19 patents and applications.
Related articles
- Wi-Fi Alliance Debuts Next-Gen Security Protections with WPA3
- Wi-Fi Alliance Unveils WPA3 Security Protocol
- How Your WiFi Can Protect Against Intruders
- Cybersecurity basics: Server and end device relationship to LoRaWAN network, Part 1
- Cybersecurity basics: Authentication and “key” management in LoRaWAN
- 6 Recommendations for Securing 5G Networks: New Opportunities, New Threats





Tell Us What You Think!