The O-RAN Alliance has developed specifications for communications interfaces between components of an Open RAN. This FAQ explains the functions of each.
An Open RAN network disaggregates traditional RAN into three fundamental components: radio unit (RU), distributed unit (DU), and centralized unit (CU). Open RAN introduces considerable flexibility, with mobile network operators (MNOs) using commercial off-the-shelf (COTS) components — rather than proprietary hardware — to run virtualized network functions. This article discusses key Open RAN interfaces and protocols defined by the O-RAN Alliance and describes their coordinated function in network operations.
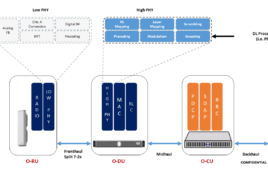
The protocol layers and interfaces of Open RAN architecture
Unlike a traditional RAN, Open RAN features a modular, layered architecture that significantly improves network flexibility and management. It supports open interface specifications for fronthaul, mid-haul, and backhaul, seamlessly interlinking the RU, DU, and CU with the core network. Figure 1 contrasts traditional RAN with Open RAN.
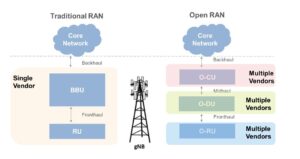
Figure 1. Comparative diagram of traditional RAN vs. Open RAN, illustrating the transition from single-vendor to multi-vendor ecosystem. (Image: Mathworks) https://www.mathworks.com/discovery/o-ran.html
Central to Open RAN’s software-defined networking (SDN) paradigm
are multiple protocol layers, including:
- Radio resource control (RRC): Maintains communication between mobile devices and networks.
- Service data adaptation protocol (SDAP): Maps data streams to defined quality of service (QoS) levels.
- Packet data convergence protocol (PDCP): Facilitates header compression, encryption, and the transfer of user plane data.
- Precision time protocol (PTP): Synchronizes and delivers accurate timing information.
Together with various interfaces defined by the O-RAN Alliance, these protocols manage data transmission connections, ensure QoS, and perform security provisioning across the RAN.
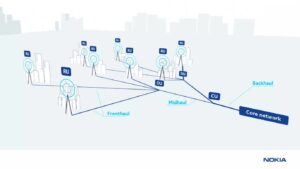
Figure 2. Open RAN consists of radio units connected through distribution units and centralized units to a network core. (Image: Nokia https://www.nokia.com/about-us/newsroom/articles/open-ran-explained/)
The E2 interface, for example, manages the transmission of control signals among the CU, DU, and RAN intelligent controller (RIC), facilitating network adjustments and resource optimization. Operating over the stream control transmission protocol (SCTP), the E2 interface supports real-time functions crucial for network adaptivity and resiliency. As Figure 2 shows, one DU handles many RUs and one CU handles many DUs.
Open RAN specifications integrate additional interfaces — including O1, A1, and F1 — to support interoperability across different vendors and systems. Compliant with internet engineering task force (IETF) standards, the O1 interface employs RESTful APIs and network configuration protocol (NETCONF) to efficiently manage network functions.
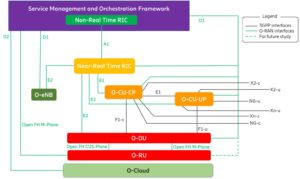
Figure 3. The O-RAN Alliance specifications define Open RAN architecture and its interfaces. Image: O-RAN Alliance
In conjunction with the A1 application protocol (A1AP), the A1 interface enforces network policy and optimizes performance. Using a Cloud RAN (C-RAN) approach, the F1 interface relies on network functions virtualization (NFV) to bolster RAN adaptability and support dynamic scaling. Figure 3 shows the Open RAN architecture.
Linking the CU and DU
Open RAN introduces additional improvements to RAN architecture. For example, the F1 interface links the CU and DU, enabling integrated handling of control and user plane functions. The independent scaling of signaling and user data is managed through the F1-C for the control plane and F1-U for the user plane.
The separation of control and user planes optimizes network efficiency and resource allocation. The U-Plane, responsible for transmitting user data, maximizes throughput and efficiency through the packet data convergence protocol (PDCP). The C-Plane, which transfers control information, maintains robust network signaling and security. Notably, the latter employs the IP multimedia subsystem (IMS) protocol to ensure interoperability with non-Open RAN networks.
Additionally, Open RAN relies on the eXtensible Messaging and Presence Protocol (XMPP) to further boost the efficiency and flexibility of communications between different network elements.
Exploring Open RAN security protocols
Open RAN dynamically adapts the default security capabilities of COTS components to meet emerging threats. Organizations such as the O-RAN Alliance play a crucial role in establishing frameworks to protect Open RAN’s multi-vendor ecosystem from compromised or counterfeit electronic components, backdoors, and exploitable vulnerabilities.
For example, the service management and orchestration (SMO) framework centralizes Open RAN control and introduces RAN management automation to streamline network operations. It also integrates the network’s controllers, including the RIC, to enforce network functions and security policies using transport layer security (TLS) and internet protocol security (IPsec).
In this context, RIC manages E2 message access and subscription requests, along with xApps that enhance RAN performance by automating decisions with real-time analytics and machine learning (ML) algorithms. Defined by the O-RAN Alliance, these xApps adhere to strict security protocols throughout their lifecycle, ensuring authenticated and encrypted communications, particularly over the A1 interface which leverages HTTP/2 for secure open API access.
In addition to the above, O-RAN Alliance security frameworks and protocols enable robust protection for network operations and applications across the multi-vendor Open RAN ecosystem, including:
- Interface communications: Prevents unauthorized access by ensuring secure encryption and authentication. To maintain the integrity and confidentiality of RAN communications, TLS and IPsec protocols protect the A1 interface against eavesdropping and tampering.
- Beamforming functionality: Manages beamforming techniques to securely optimize signal directionality and strength. Open RAN complies with common public radio interface (CPRI) and enhanced common public radio interface (eCPRI) standards, applying encryption and protocol integrity checks to prevent unauthorized modifications.
- AI/ML deployment: Enhances network capabilities by securely integrating AI/ML applications for optimal traffic and resource management — using the A1 interface for policy control, the X2 interface for model sharing, and REST APIs for managing RIC applications.
- Software updates and certificate management: Delivers timely software upgrades and reinforces secure communications by automating digital certificate issuance and validation with the simple certificate enrollment protocol (SCEP) and online certificate status protocol (OCSP).
Summary
By disaggregating traditional RAN into three fundamental components, Open RAN creates a modular and scalable SDN-based architecture that runs virtualized network functions on COTS hardware. Open RAN facilitates efficient and flexible management for MNOs, offering seamless integration of 5G technologies while extending the network’s high-speed, low-latency capabilities.
References
How Does 5G’s O-RAN E2 Interface Work?, 5G Technology World
Open RAN Explained: All You Need to Know and More, Rakuten
Understanding O-RAN: Architecture, Interfaces, Algorithms, Security, and Research Challenges, arXiv
Open Radio Access Network Security Considerations, CISA
An Intelligent Platform: The Use of O-RAN’s SMO as the Enabler for Openness and Innovation in the RAN Domain, Ericsson
Open RAN Explained, Nokia
What is O1 Interface in Open RAN?, Telecom Hall


Great article